Unveiling Vulnerabilities: A Deep Dive into WiFi Camera Security
Introduction
In a recent security analysis of a WiFi camera, my colleagues, Gabriel Duschl and Maximilian Riedl, and I discovered numerous vulnerabilities. This article walks you through the security analysis and our key findings.
Security Analysis
We bought a budget-friendly WiFi camera on AliExpress and conducted a security analysis.

To activate the webcam, you must register an account, select your WiFi base station, and input your password. After that, the camera is ready to use and displays the video feed.
You also receive a notification if a human is detected :-)
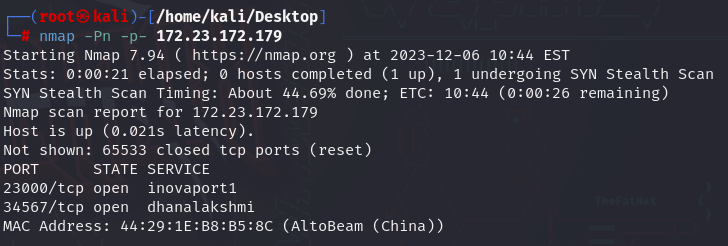
After a quick nmap scan, we identified two open ports, as shown in the following screenshot.
After exploring the mobile app, we wanted to inspect the firmware. Unable to find it online, we disassembled the camera and researched all the processor datasheets.
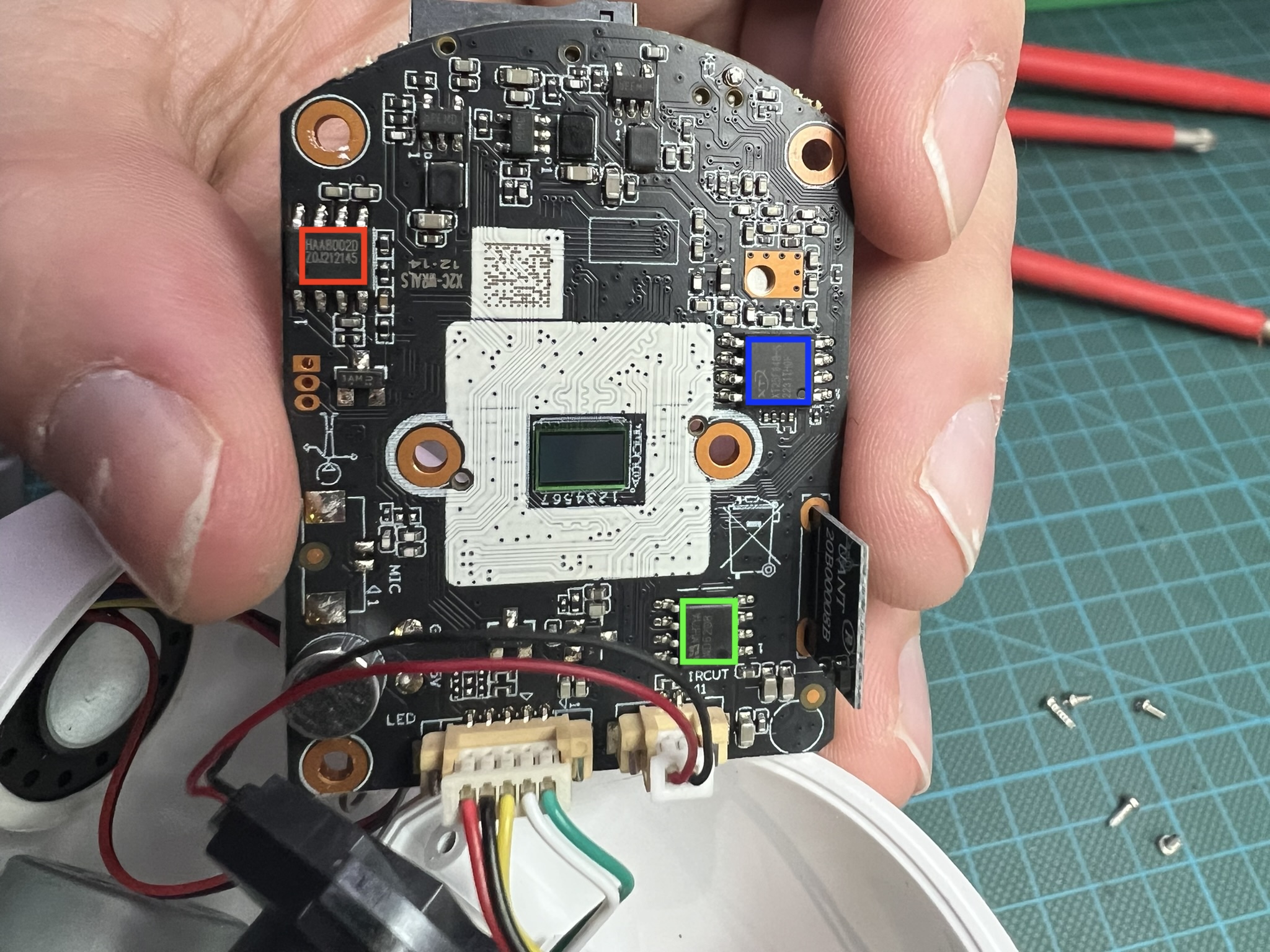
- XT25F64B-S (blue) - NOR Flash (Download datasheet here). The firmware is stored here.
- haa8002b (red) - Power Amplifier (not really interesting)
- WD6208 (green) - IC for controlling the webcam motor (not really interesting)
We can easily dump the firmware using an SPI programmer like the CH341 with a SOIC8 adapter. Luckily, Neoprogrammer supports the XT25F64B (the also popular AsProgrammer does not). After overcoming challenges with voltage levels and erratic USB ports, we successfully dumped the firmware.
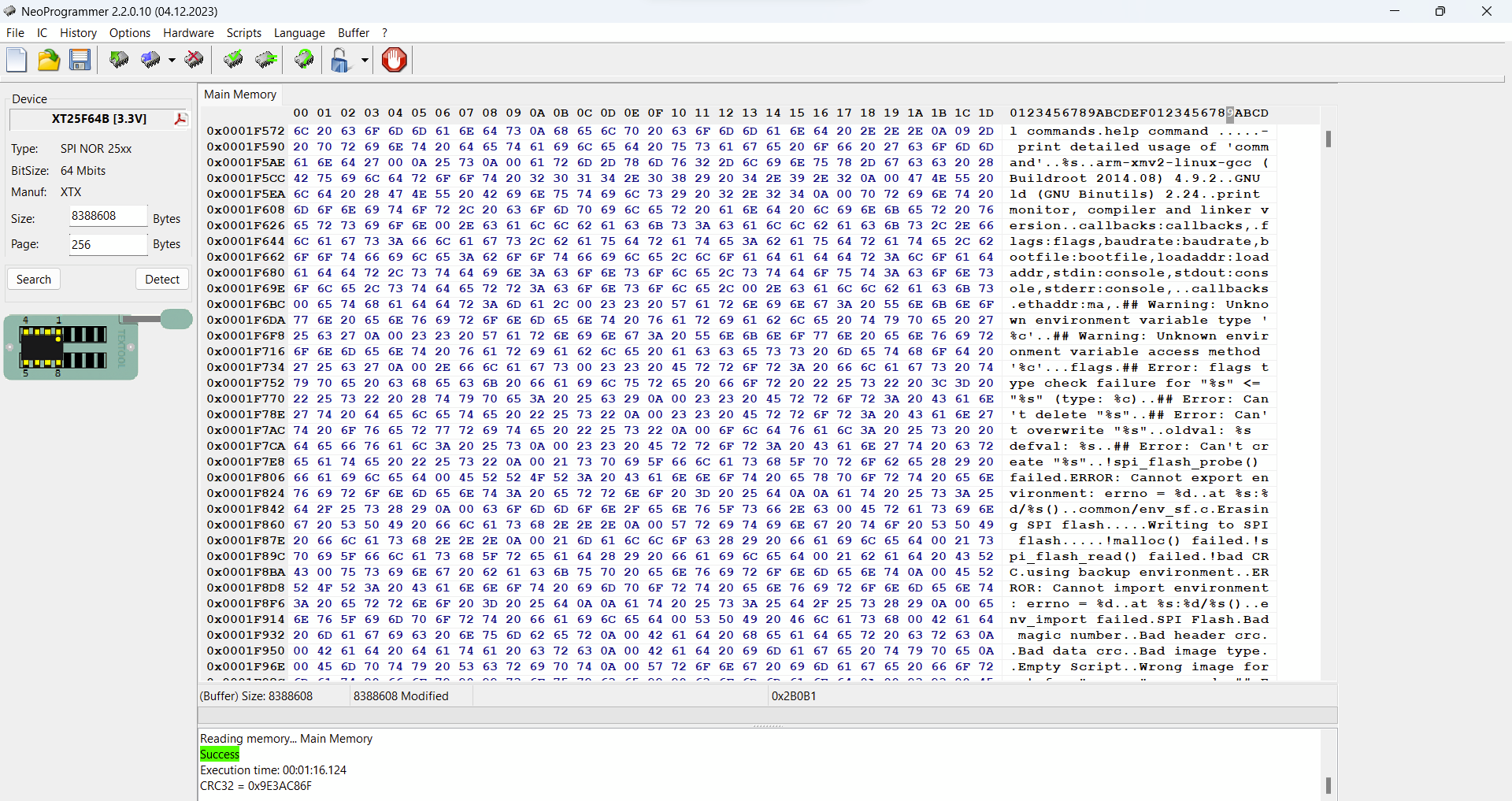
In case you are interested. You can download the firmware here
With firmware images, binwalk, and unblob, you are in good hands. So here is the unblob overview.
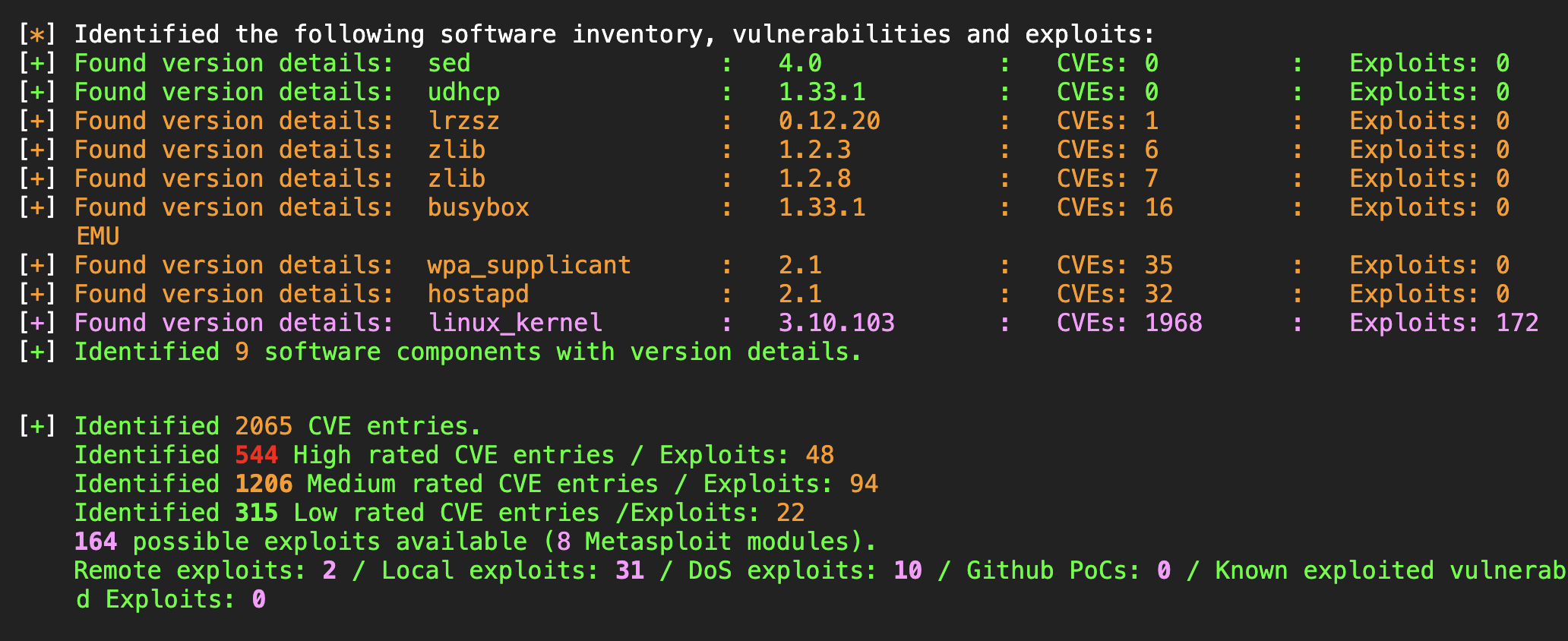
For a first analysis, we threw the firmware image into embark. This revealed a more than 7-year-old kernel version 3.10.103. Due to the aging kernel, version 3.10.103, the firmware is associated with over 2000 publicly known CVEs, highlighting a severe security risk. More than 500 of those vulnerabilities are rated with high severity, and there are even ready-to-use Metasploit modules. While not all CVEs may be directly applicable, the sheer volume of potential threats underscores the need for immediate updates.
As it turns out, our WiFi credentials are also stored in plaintext. Unfortunate but common for ESP-based chips. I think I’ve already gotten used to it.

Mobile App
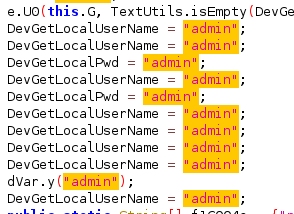
We didn’t analyze the mobile app in great detail. However, we did notice some questionable aspects in the code, like the consistent use of “admin” for all usernames and passwords.
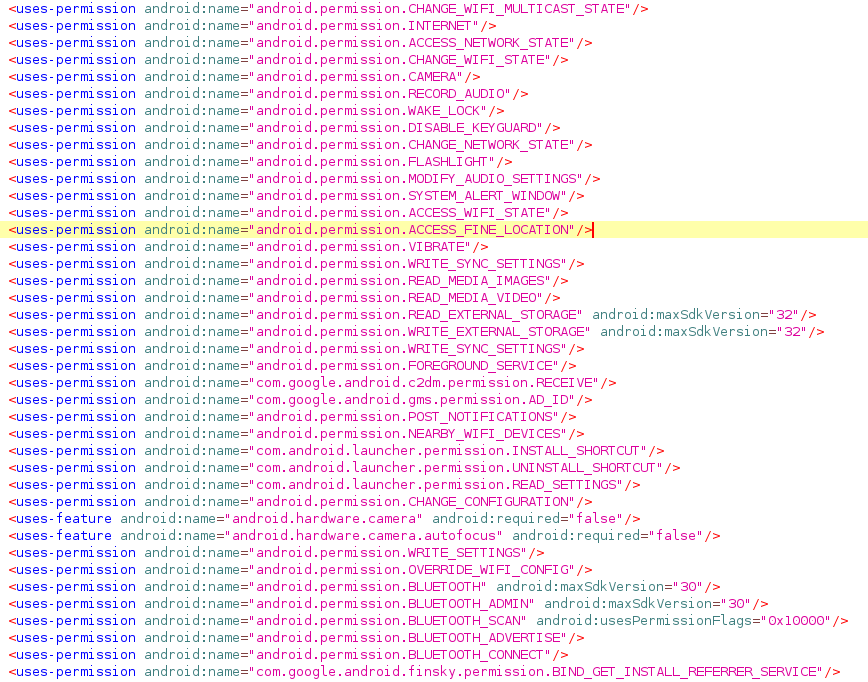
Moreover, the app permissions cover virtually every aspect you can imagine.
Possible further research
As previously shown, the camera opens two ports 23000/tcp (inovaport1) and 34567/tcp (dhanalakshmi). The next step would be to identify the binaries within the firmware behind those ports. Further research might involve reverse engineering and fuzzing of those binaries. So if you are interested, please let me know.
Overview of the findings (so far)
Outdated Kernel (Version 3.10.103 - August 2016)
The firmware relies on an outdated Linux kernel, dating back more than 7 years. This aging kernel, version 3.10.103, is associated with over 2000 publicly known CVEs, highlighting a severe security risk. While not all CVEs may be directly applicable, the sheer volume of potential threats underscores the need for immediate updates.
Suspicious URLs Transmitting User Data
Our analysis revealed numerous suspicious URLs embedded within the firmware actively transmitting user data to external domains. This discovery raises serious concerns about user privacy and the potential misuse of sensitive information.
WiFi Credentials Stored in Plaintext
During the setup process of the camera, you have to enter the WiFi password. The credentials are stored in plaintext.